Jailbreaking iOS Devices for Testing
When looking at digital evidence, forensic examiners want as much data as possible. This can be particularly tricky when working with an iOS device. Apple has these devices pretty locked down and can make it difficult to retrieve any data. If you have the passcode to the device, you can create a regular backup which will give you a lot of data. But if you want to do some testing to see how certain apps behave or what kind of digital evidence is left behind, you may want to get yourself a test iOS device and jailbreak it. Jailbreaking allows you to retrieve and sift through more data than looking through a regular iOS backup. We’ll walk you through how you can do this and how you can communicate with your device through a terminal.
1. Finding a good candidate for your test device.
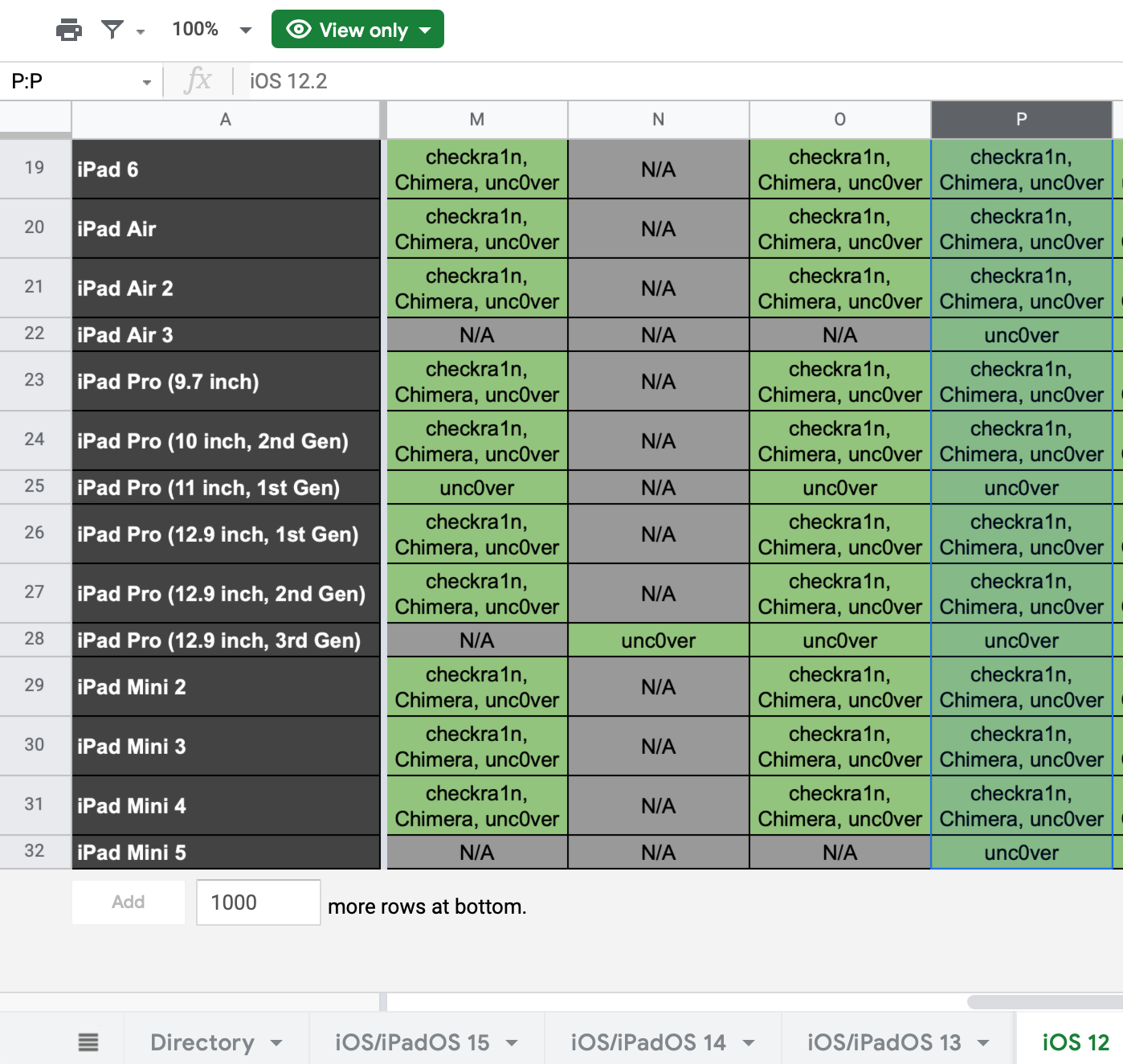
You’ll want to look at your device and see exactly what you’re working with. The best device to jailbreak will be something that isn’t running the latest iOS version and probably isn’t the latest model phone. This is because Apple is usually pretty good about patching any vulnerabilities that allow for jailbreaking. To verify if you have a good test device, figure out what Apple hardware you have and what version of iOS you’re running. These are both important items to know before proceeding. If the hardware or software version isn’t supported, you’ll be out of luck. A good reference point to check is this well-maintained Google Sheet located here: https://docs.google.com/spreadsheets/d/11DABHIIqwYQKj1L83AK9ywk_hYMjEkcaxpIg6phbTf0/edit?usp=sharing
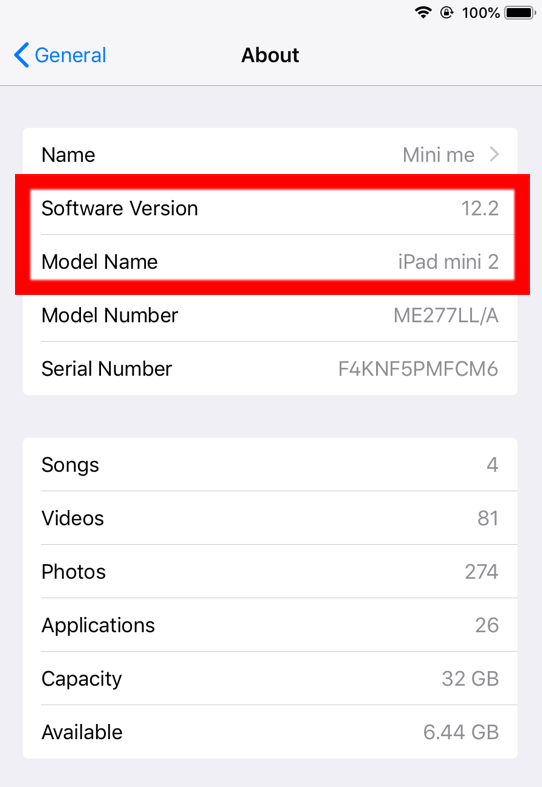
2. The first thing we need to check is the iOS version. My device is running iOS 12.2. You can check this by going to Settings -> General -> About -> Software version. While you’re there, you also want to see the Model Name. In the screenshot below, you can see I have and iPad mini 2 running software version 12.2.
3. Then we’ll head over to the Google Sheet mentioned earlier and select the appropriate tab for your iOS version and the appropriate device as shown below. Our test device is and iPad Mini2 running iOS 12.2 (Column highlighted). We can see that this device can be jailbroken with checkra1n, Chimera or unc0ver.
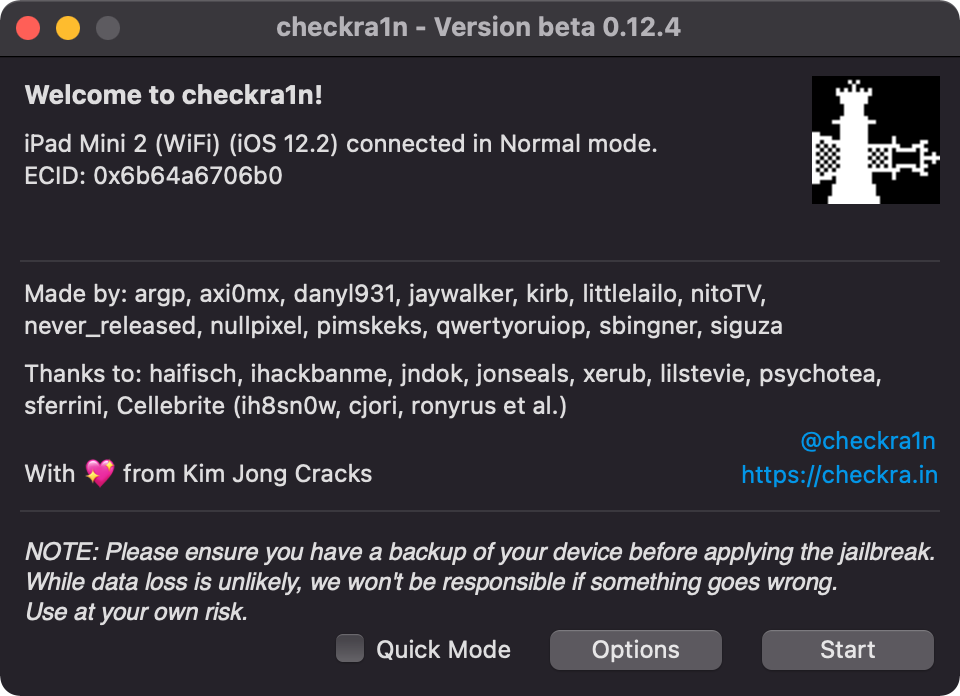
4. For our purposes, we’ll go with checkra1n. It’s the most popular one out there that supports the most devices because it employs the checkm8 exploit which targets the bootloader. This means there’s a good amount of iOS device that even Apple can’t patch.
5. For checkra1n, you can download it from: https://checkra.in. Install and run it. It’ll query the device connected to your computer and you just have to hit ‘Start’.
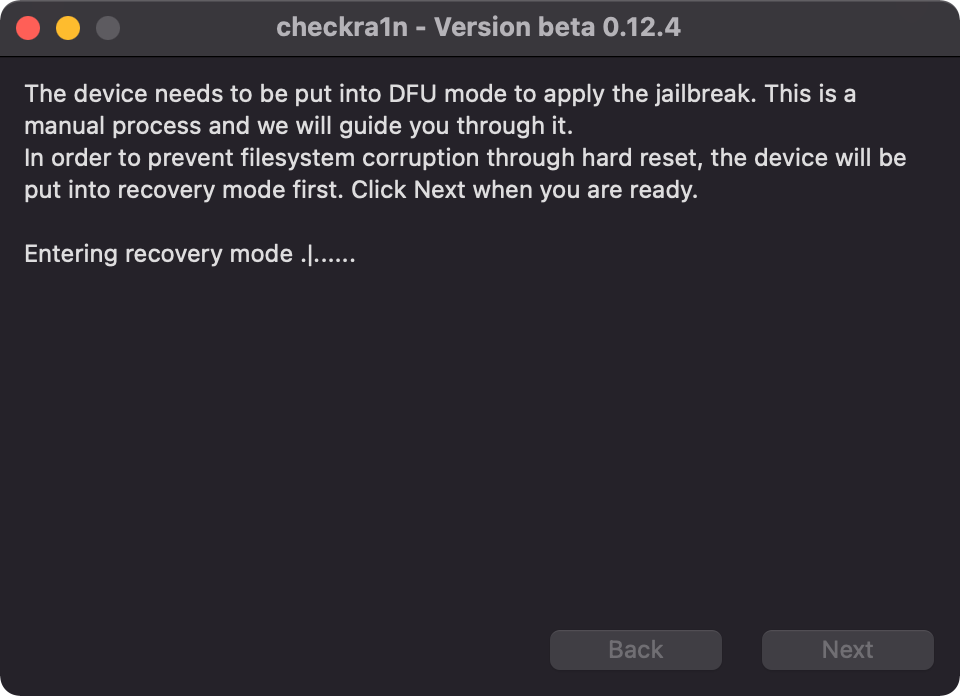
6. Follow the steps to allow the checkra1n to put the iOS device that’s connected to your computer in Recovery mode.
7. Once in Recovery mode, you’ll need to put the device into DFU mode. Depending on your device, you’ll need to hold and then release a certain combination of buttons. checkra1n will tell you which buttons to hold down and provide a timer for how long to hold down each one. An important note here is to avoid using a USB-C to lightning connector since there are issues with allowing the device to enter DFU mode. Instead, use a more traditional USB-A to lightning connector.
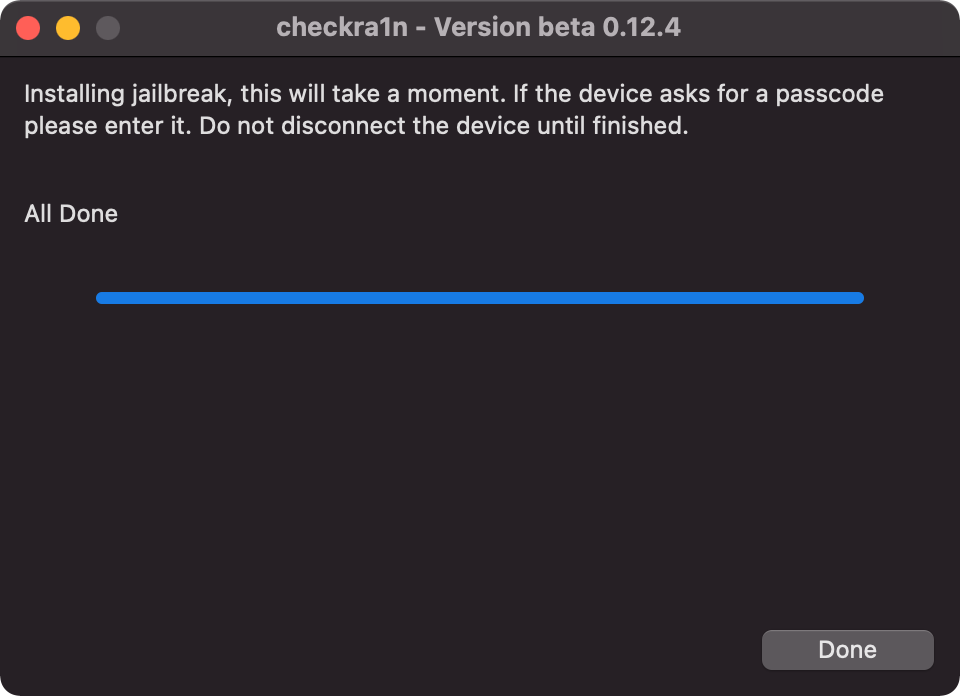
8. Once checkra1n is complete, you’ll be greeted with this screen verifying success.
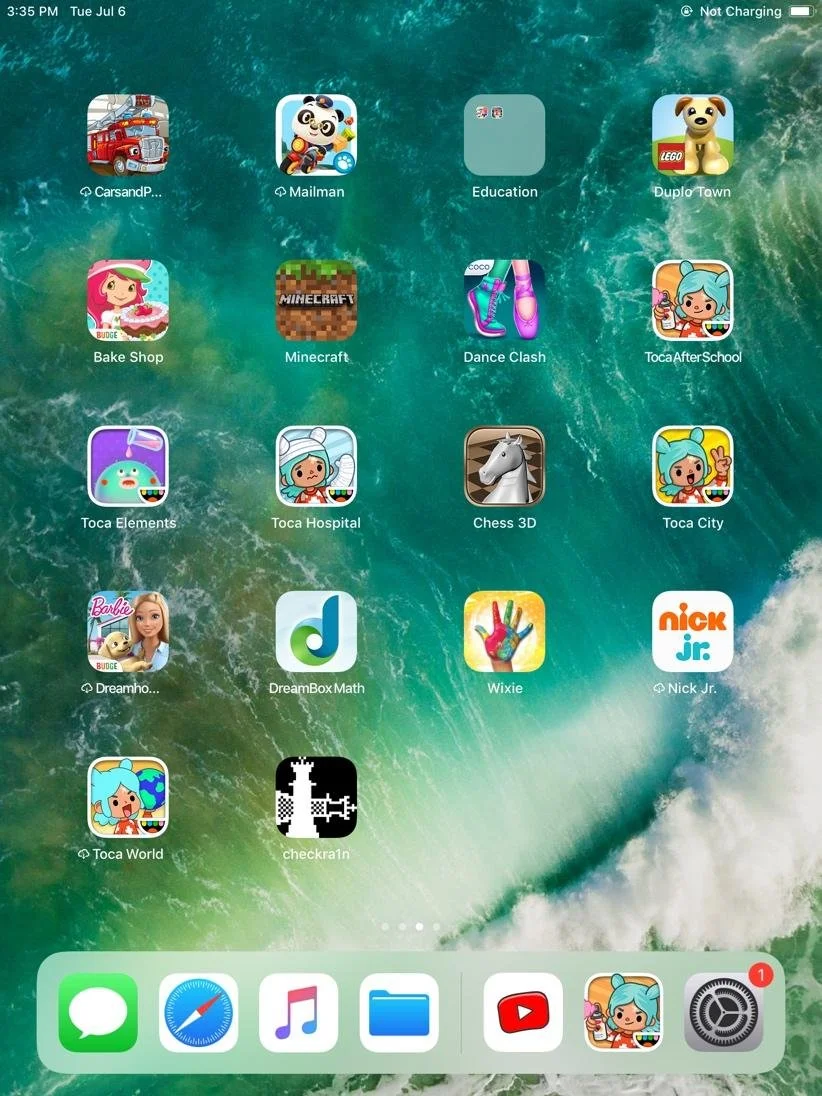
9. Check out your device and you will see the checkra1n app. (Please excuse the apps as this device was donated by an ArcPoint daughter ☺).
10. Open the checkra1n app and then click Cydia so you can download additional applications.
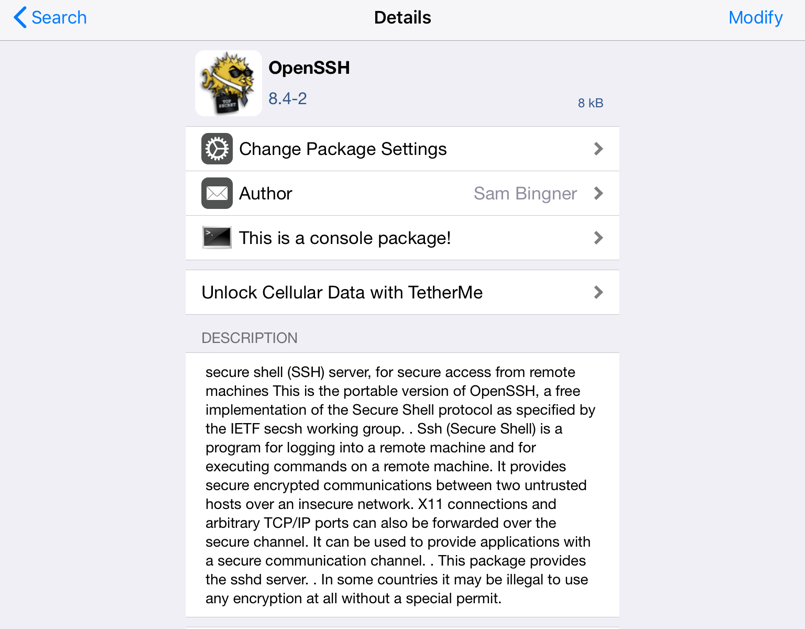
11. One application we will need is SSH. So do a search for “OpenSSH” in the Cydia app store and install it.
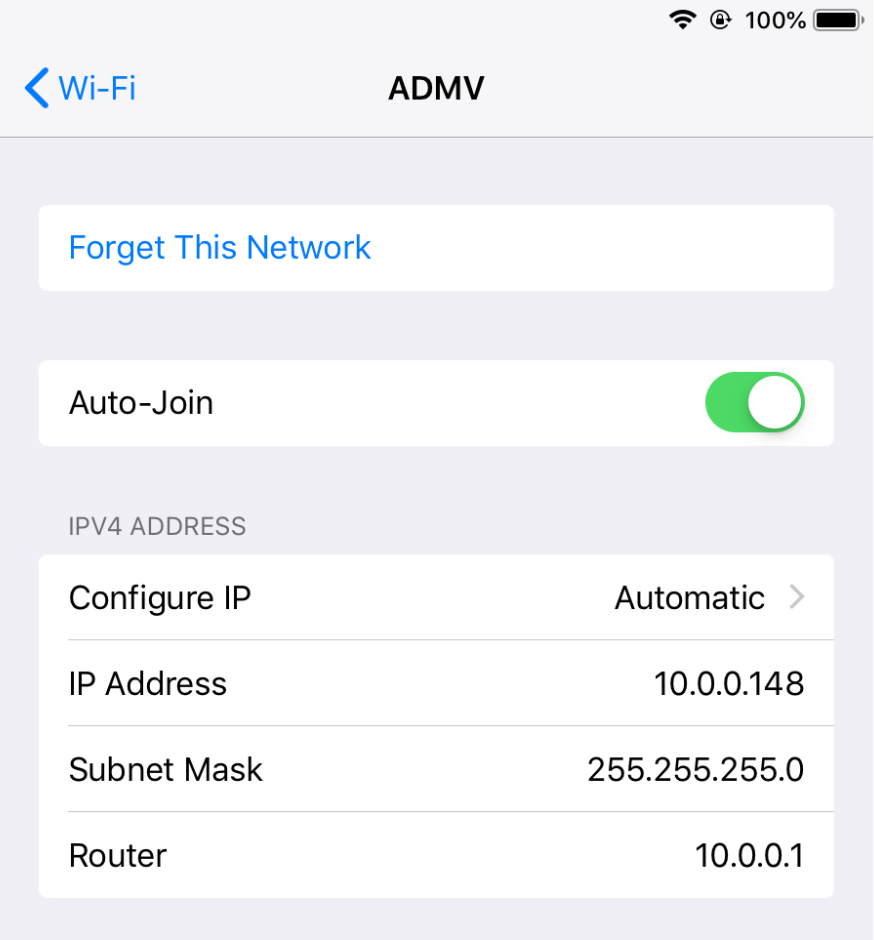
12. Once installed, we need to get the IP address from our device. We can go to Settings->Wi-Fi and jot down the IP address since we’re on the same wireless network.
13. We jump back over to our computer and open up Terminal and type in ‘ssh root@[IP address]’
14. When prompted for the password, enter in ‘alpine’, which is the default password for all iOS devices
15. Once complete, you’ll know you have root access because of the ”#”. And you’ll have additional access to files that you didn’t have before you started this whole process.
Depending on the application, you may still have certain restrictions, so you won’t be able to see EVERYTHING associated with the app, but you’ll have opened a lot more files to explore and test with. There are other methods to jailbreak, and even paid iOS virtualization software that is available, but this is a good method to use if you have an old iOS device lying around that you want to use for testing. Enjoy!