macOS Forensic Artifacts
Why we need this article
It’s pretty much given that we live in a Windows-centric world. The majority of businesses and individual users out there use Windows machines to get work done. And because of that, it’s safe to say that the majority of incidents and forensic investigations target Windows machines. It leads many digital investigators to be well-versed in Windows forensics and know exactly where key artifacts are. But eventually, we all come across that MacBook Pro or iMac that we need to forensically examine. Today’s blog takes a look at a few key types of macOS artifacts to help jumpstart your investigation and includes links to some open source tools that can help you.
Apple Property Lists (plists)
In a Windows workstation, we’re accustomed to extracting the registry hive. The registry is essentially a database that has information used to configure a Windows machine. It’s a pretty convenient database with a lot of useful artifacts. Unfortunately, it doesn’t have an equivalent on macOS. What Macs do have are .plist files with system and user configuration information.
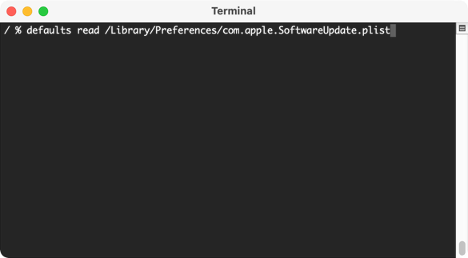
These plists are individual files located throughout the file system. Just navigate to the path listed and use ‘defaults read’ to open up and read the plist information directly in the terminal. In this screenshot, I’m checking the SoftwareUpdate.plist to see what kind of configurations are set for updating the macOS software on this particular machine.
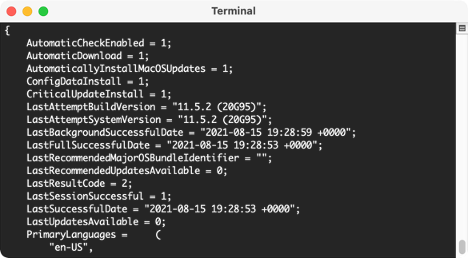
The results I get are below. You can see the ‘1’ where I’ve checked the box. So, essentially, they are ‘on’ in my specific machine.
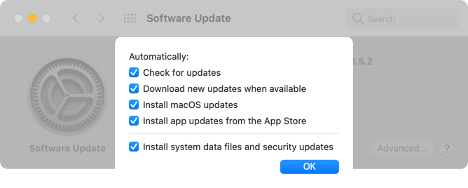
As you can see, they match the settings currently set on my mac when prompting for updates.
Different plists will contain various configurations for a mac system so take a look around to see what different configuration files you can find.
DS_Stores
At first glance, Desktop Services Store (.DS_Store) files may appear to be pesky, hidden files that you may have come across on your Windows machine. However, just because you have come across them in Windows, doesn’t mean they’re a Windows artifact. Windows has nothing to do with DS_Stores. They are actually born in macOS and are created in folders that Mac’s “Finder” accesses. So if you do run across them in your Windows machine, it’s because that drive was at some point connected to a Mac.
The purpose of a .DS_Store file is to save the configuration and customizations for that particular Finder window so that the next time you go in there, the Finder window for that specific folder will be in the same state as the last time you accessed it.
From a forensic perspective, they’re important because they show that the user of the machine accessed that particular folder at some point. As with anything, there are exceptions, so you may run into a situations where a .DS_Store is not created, such as when the Finder is in the ‘Columns’ view.
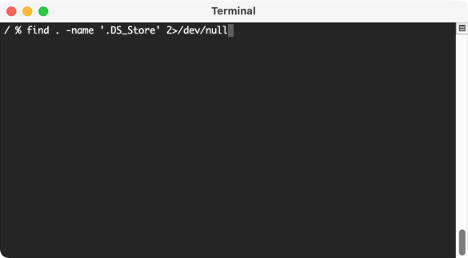
If you’re on a live machine, we can open up a terminal and search for them with the command:
On a brand new install of macOS, you won’t find much. But if you’re running this on your own system, it’ll return numerous search results. Once you have the DS_Stores, you can use the parser below to take a look at the results.
Open source DS_Store parser: https://github.com/nicoleibrahim/DSStoreParser
FSEvents
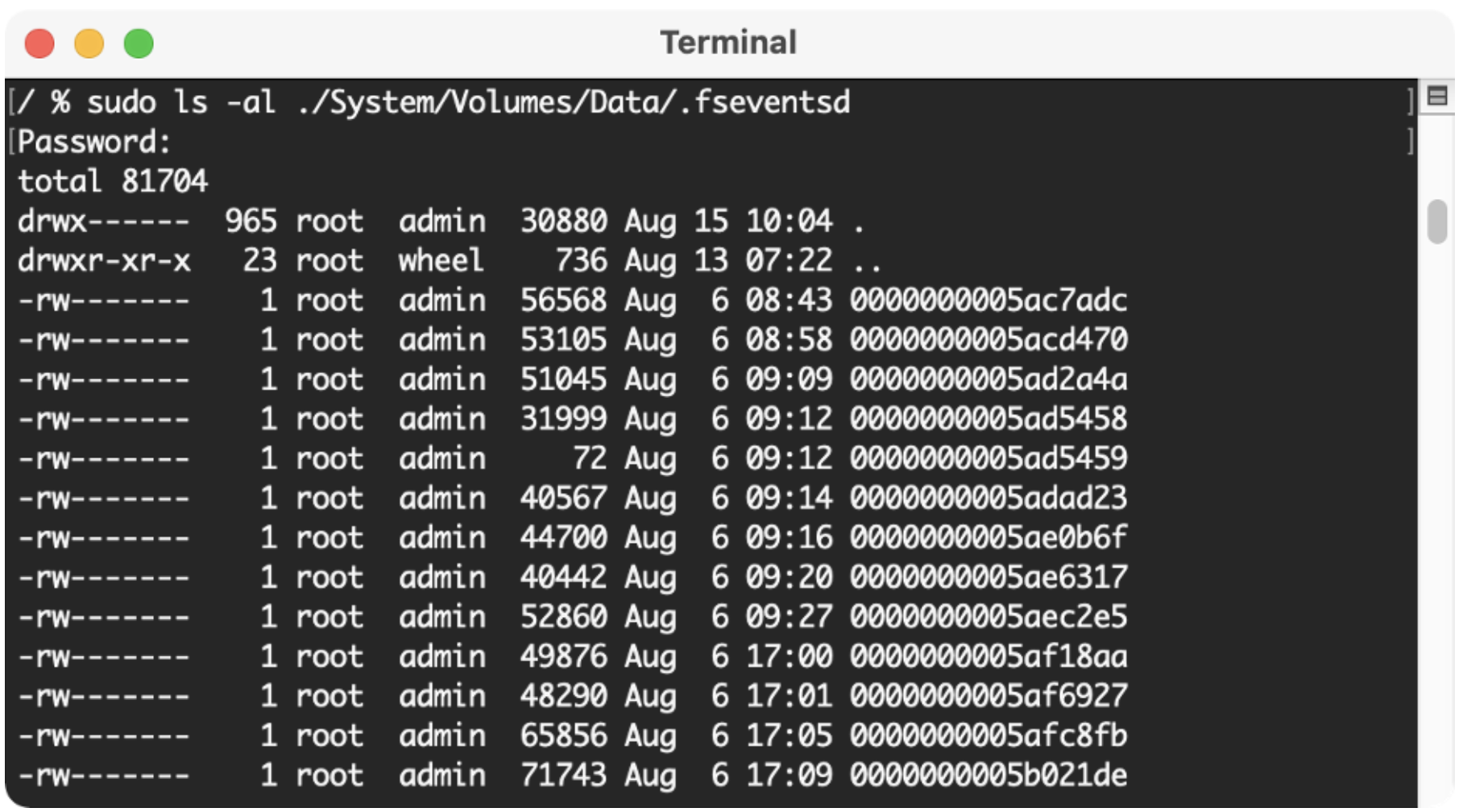
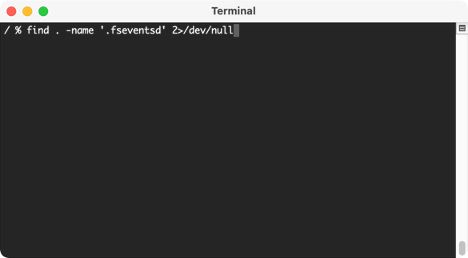
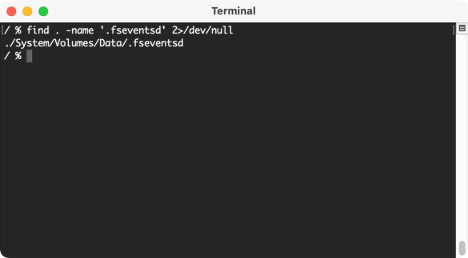
File System Events (FSEvents) are found in the root of each volume attached to macOS. It will be in the ./fseventsd directory. These files track changes made to the files or folders for that volume. These logs can tell you if files and folders have been moved, deleted, created, mounted, etc. They track all the different iterations a file and folder can potentially go through.
We can search our own Mac to find all the FSEvents. If you have external storage devices connected, FSEvents for those mounted volumes will also be found.
In this screenshot, I don’t have any external devices connected to my mac so there’s only one location where FSEvents is present.
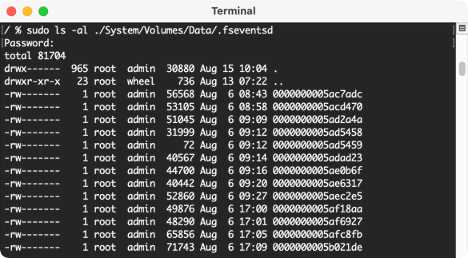
The .fseventsd/ directory is filled with numerous gzip files that contain the logs for all the changes to the files.
After we’ve found the .fseventsd/ folder, we can copy them out and use the parser linked below.
Open source parser for FSEvents: https://github.com/dlcowen/FSEventsParser
Conclusion
Macs can be daunting for those not well-versed in the “dark arts” of mac forensics. The artifacts and files discussed above are just a few that can help you find some key pieces of information related to your case.
As with anything else in forensics, as you dig around and pull on strings, you either find great stuff or discover that you have even more questions. (Or both!!) Hopefully, these tips will give you a starting point for tackling a macOS examination.