Rooting Microsoft Surface Duo
Intro
The Microsoft Surface Duo launched on September 10th, 2020. Instead of using Windows Phone OS, Microsoft decided to switch it up on everyone and introduced the Microsoft Surface Duo; a device that was built on Android.
Much like our iOS blog on jailbreaking, we wanted to tackle rooting an Android device and at the same time, look at Microsoft’s newest device and prep it for forensic testing for future analysis.
⚠️ In this blog, we go back and forth between phone and computer often. To try and make things easier for you, we’ll use 💻 if the command/instruction is from your computer and 📱 if you need to do it from the Surface Duo.
Prep Work
💻 In order for your computer to communicate with the Android device, we need to download the command-line tools located here: https://developer.android.com/studio/releases/platform-tools. Download the appropriate one for your workstation. In my instance, I would download “SDK Platform-Tools for Mac”.
📱 On the Duo, we enable the communication to the platform-tools by performing the tried-and-true method of enabling Developer Options. On the Duo, go to Settings -> About. Then proceed to tap Build Number seven times and you’ll successfully enable Developer Options.
📱 Let’s make sure that our Surface Duo is set up so it can talk to your machine by enabling the USB connection.
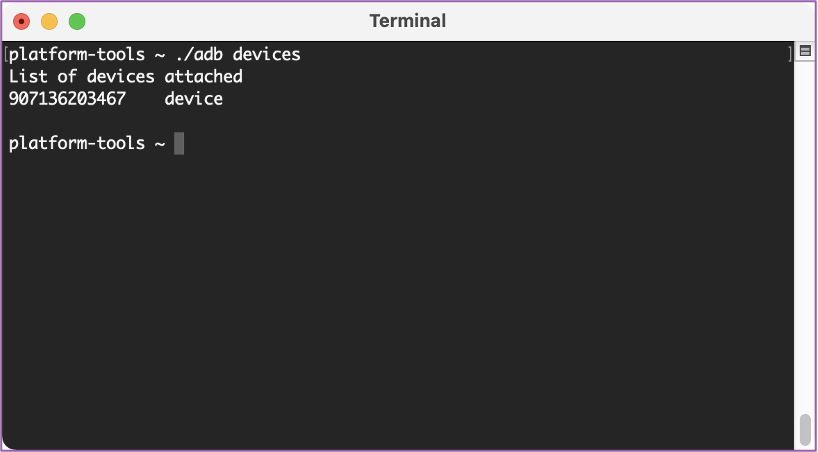
💻 Once we are connected, let’s go back to our computer and confirm. We’ll navigate to the platform-tools folder. We can type “./adb devices” to verify that we do see the Duo and it’s communicating with our workstation.
Prep work - Surface Duo specific
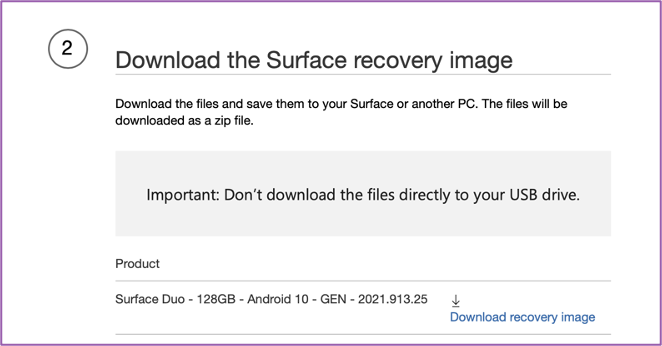
💻 Download the Surface Recovery Image from here: https://support.microsoft.com/en-us/surface-recovery-image
You’ll need the Serial Number from the device. It can be found on the SIM tray or in Settings -> About -> Model & Hardware.
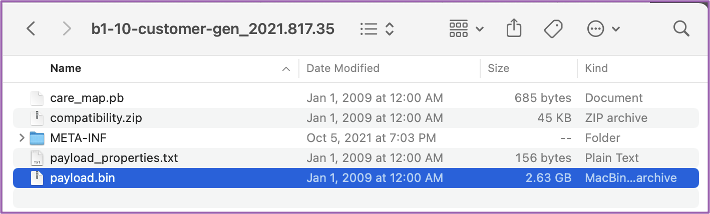
💻 Once the recovery image is downloaded, you need to unzip it and locate the payload.bin file.
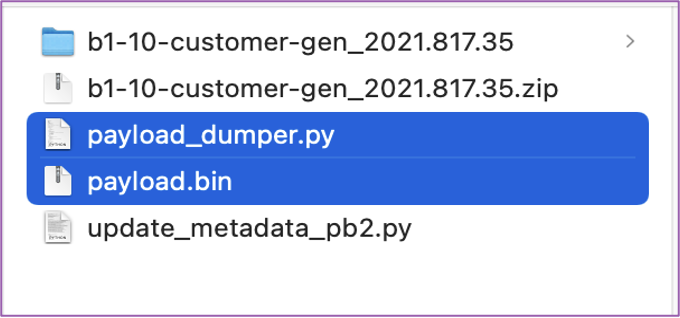
💻 In order to extract the boot.img file from payload.bin, we will need to download a python script called payload_dumper from here: https://drive.google.com/file/d/1QpsywAbNroDKEDz4TytQl8UlK6v2gJSi/view. This will allow you to take the recovery image we downloaded from Microsoft and extract the various partitions. Copy the payload.bin file (from above) to the payload_dumper folder. You should have this:
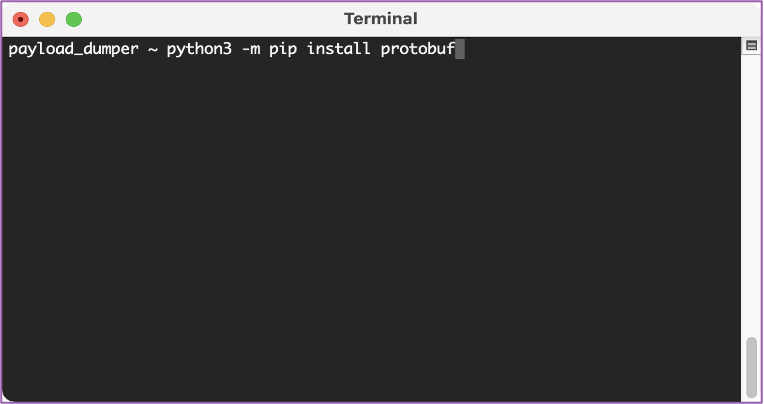
💻 Protobuf is a requirement for the payload_dumper so we can install it using the following command “python3 -m pip install protobuf”.
💻 At this point, you should have:
✅ Located the payload.bin file
✅ Downloaded payload_dumper
✅ Copied the payload.bin file to the payload_dumper directory.
✅ Installed protobuf
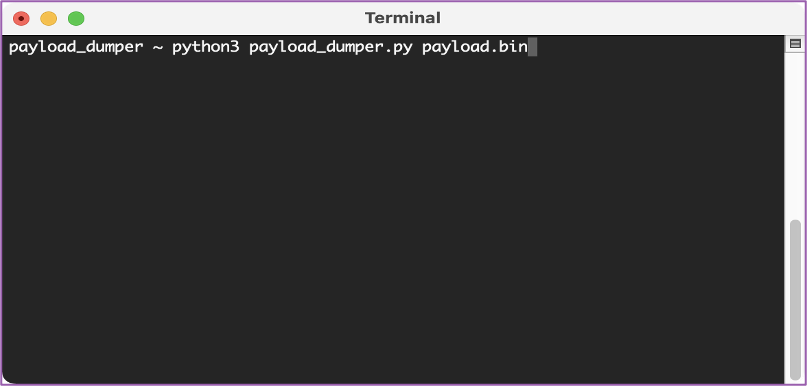
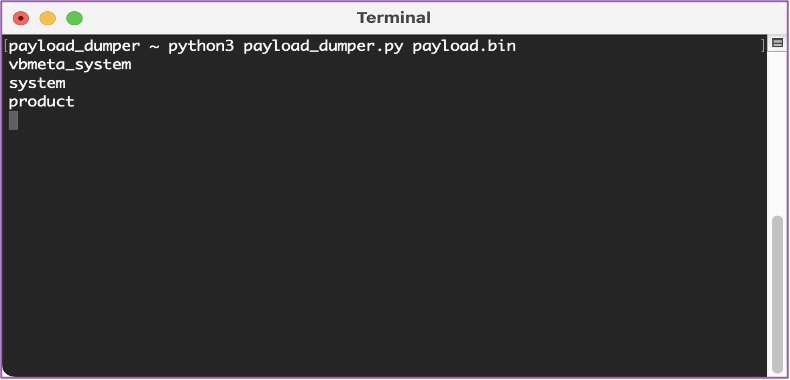
💻 Now we’re ready to run payload_dumper on the payload.bin file using this command “python3 payload_dumper.py payload.bin”.
💻 You’ll then see the different partitions start to extract into the payload_dumper folder.
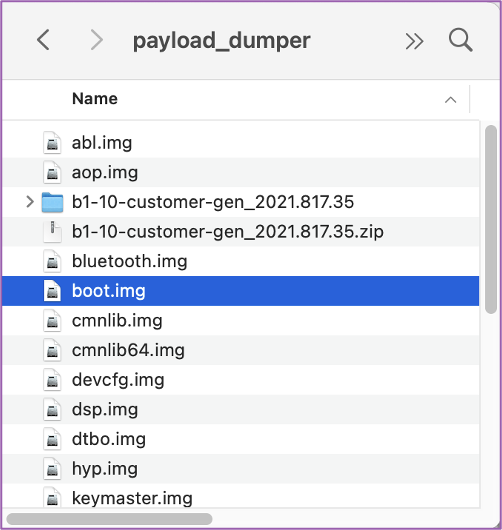
💻 Once complete, all the different partitions from the recovery image will be in your folder. The only one we need is the boot.img file to move onto the next step.
Let the Rooting Begin!
💻 If you’re working on a Mac like I am, download the Android File Transfer (AFT) too here: https://www.android.com/filetransfer/ as an easy way to put a file on your device.
💻/📱 From your computer, download the Magisk apk from this location: https://github.com/topjohnwu/Magisk/releases/download/manager-v8.0.7/MagiskManager-v8.0.7.apk and place it on the root of your device using AFT.
⚠️ The most current version of Magisk didn’t work during the creation of this walkthrough but the one linked above worked just fine.
💻/📱 Place the boot.img on the root of the device using AFT.
💻/📱Create a text file on your computer and paste the following inside of it: https://raw.githubusercontent.com/Lethany/magisk_files/0755a7d5f596dc2a351270120b31b665fb561294/stable.json. Then move that over to the root of the device using AFT.
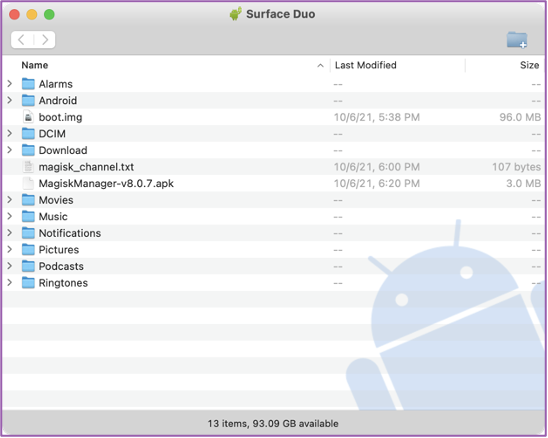
💻 /📱You’ll see the three files I have on the root of my Surface:
✅ boot.img
✅ MagiskManager-v8.0.7.apk
✅ txt file with address above (mine is magisk_channel.txt)
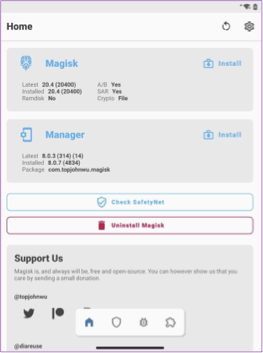
📱 Now that we have all the files, we are ready to modify the boot image that we downloaded with Magisk. Go ahead and install Magisk using the APK we saved on the root of the Duo. Once it’s installed, you should be greeted with the screen below.
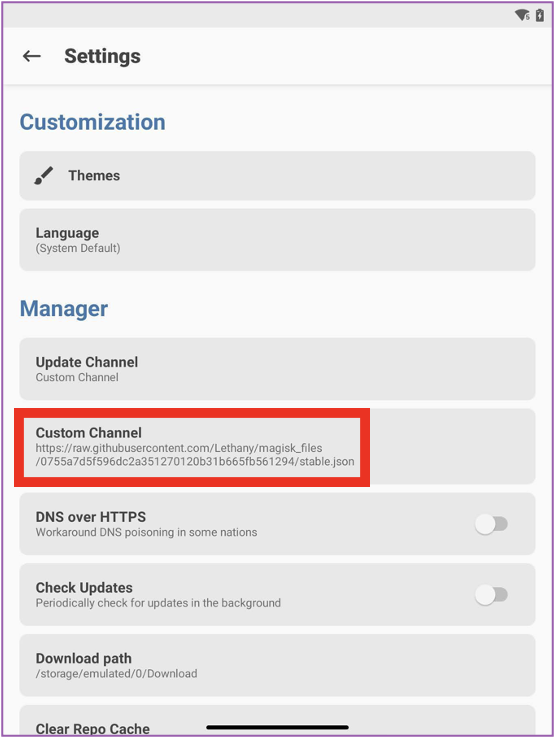
📱 Let’s go to the Magisk settings and copy the address from the text file above and set it as a Custom Channel. You should have a similar screen to what’s below.
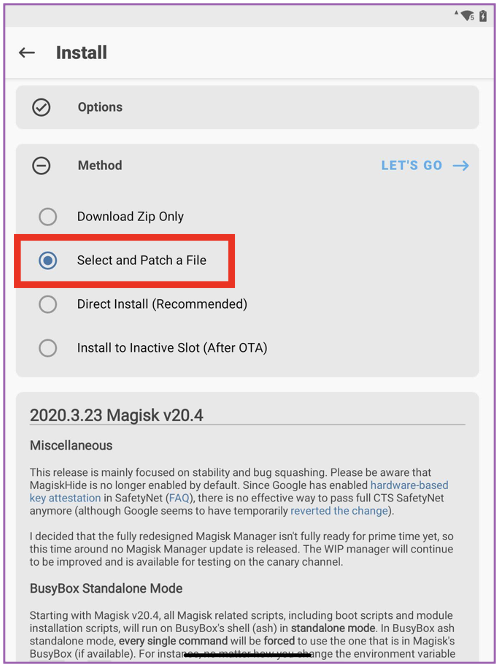
📱 Let’s go back to the main screen in Magisk and then tap on Install. We want to “Select and Patch a File”. We’ll select the boot.img file which is located on the root of our device.
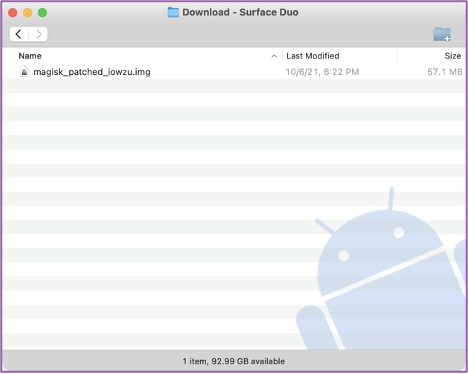
📱 Once Magisk is complete, you’ll see a patched img file in the Downloads directory on your Duo. We can see it here in AFT.
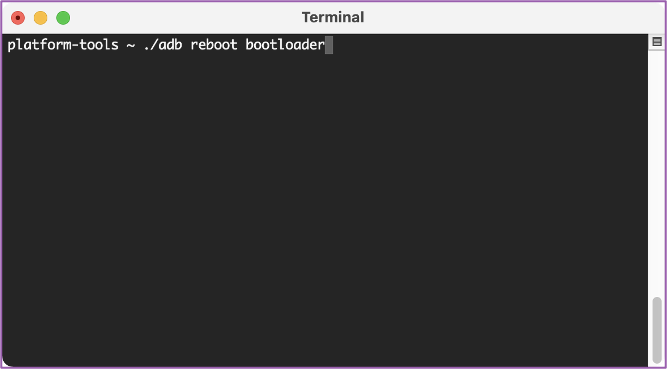
💻 Now we can do a reboot into the bootloader of the Surface Duo from the terminal.
💻 Once the phone has rebooted, you’ll see that Surface is in Recovery mode.
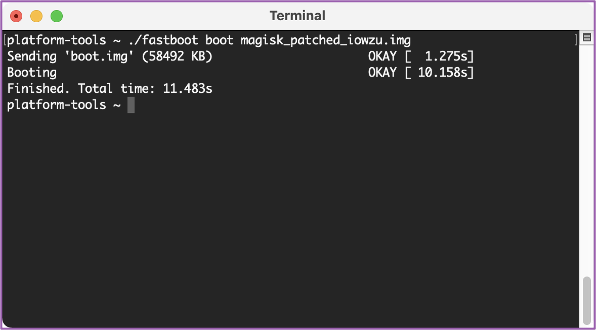
💻 We need to do use fastboot and along with the image that we patched with Magisk to boot into a temporary root using the command ‘./fast boot boot magisk_patched_iowzu.img’.
⚠️ Once the phone reboots, we’ll have temporary su access, but we want it to be permanent, so we’ll make a few more changes.
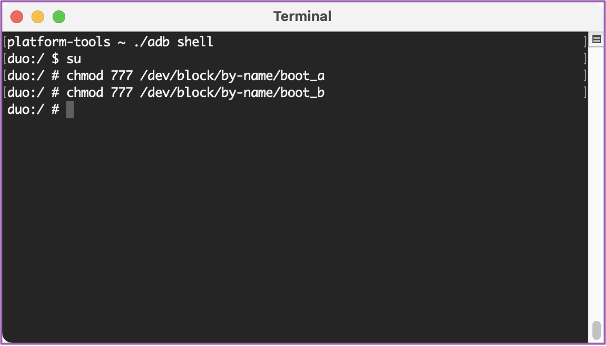
💻 Using chmod will give us the permissions to make the modifications in the next step so that we can ensure the root is a permanent one and will persist through rebooting of the Surface Duo.
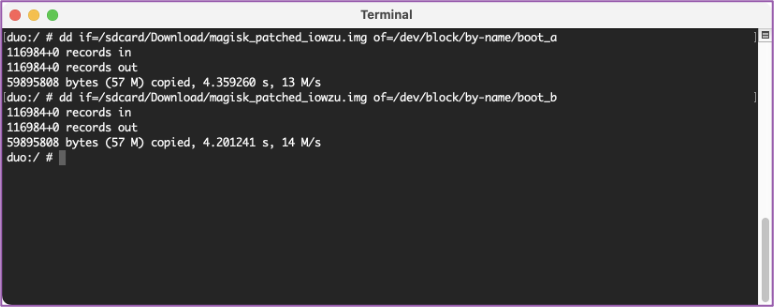
💻 In this step, we are pushing the patched boot image file to overwrite the stock boot files. Overwriting the stock boot files with the patched ones will ensure the root persists.
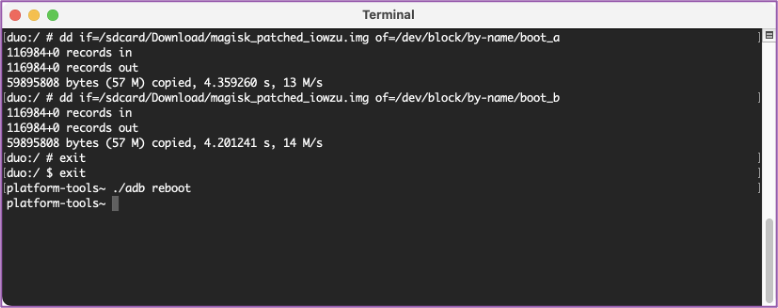
💻 Now let’s exit out of the phone and do an “./adb reboot”. Once we’ve rebooted, we’ll have a permanently rooted Surface Duo ready for further testing.
A Quick Look
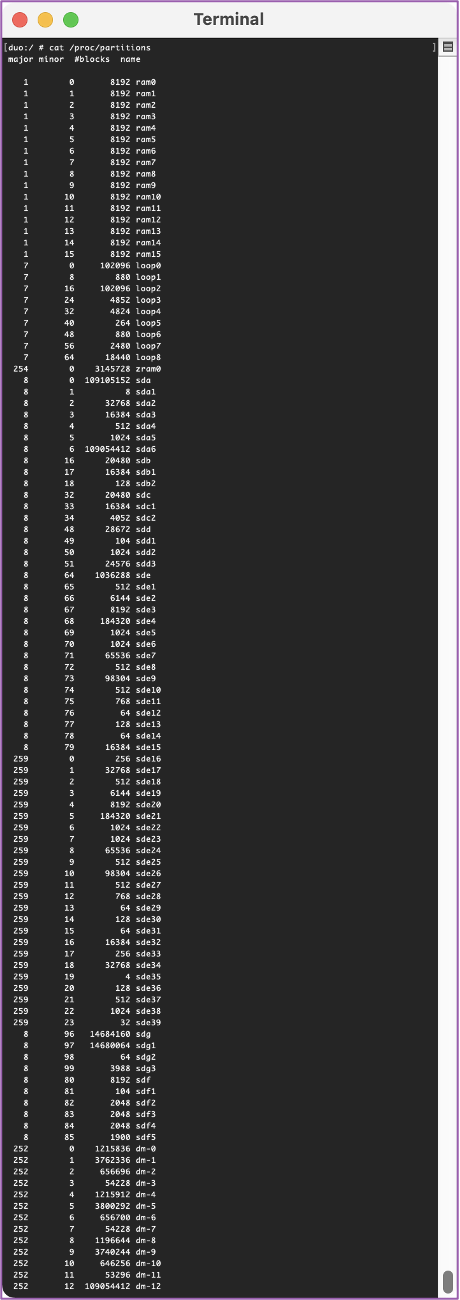
💻 Now let's take a quick look at the device. We can open a shell and look at the different partitions with the command, “cat /proc/partitions”. As you can see, there are a bunch of different partitions, but we don’t know what any of those partitions are.
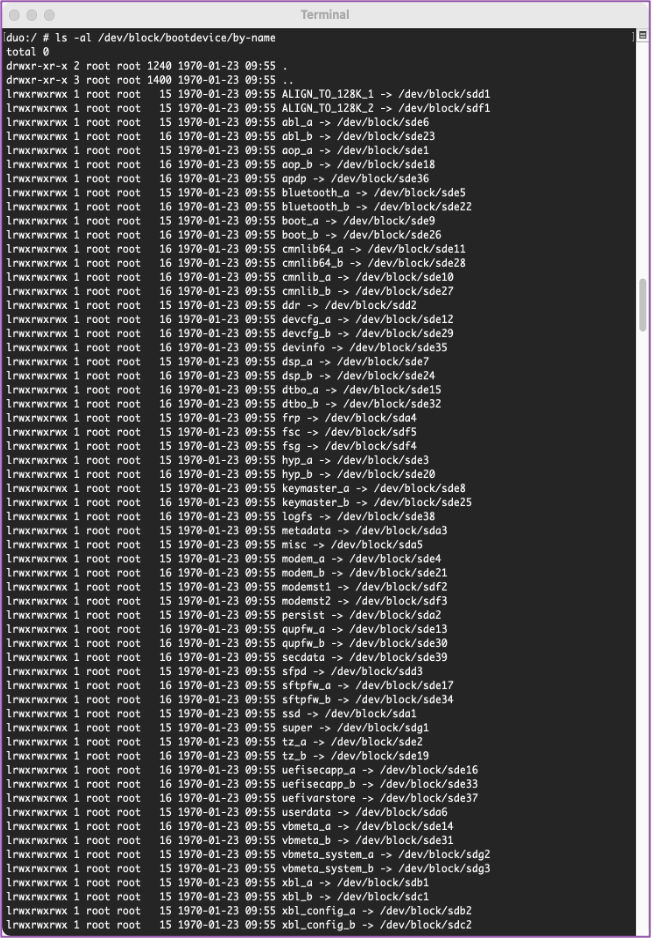
💻 If we want to take a lot at the different partitions and what they pertain to we should “ls -al /dev/block/bootdevice/by-name”.
💻 If we want to focus in on the data partition, we can search for it using ‘mount | grep ‘ /data’ command’.
Conclusion
We’ve come quite a long way! We started with a device that was pretty locked down and didn’t want to share its data to a device that we can now fully test and exploit. We also took a quick look at the different partitions and determined what each partition referred to. It leaves us in a much better position to continue to test and populate the Surface Duo with test data. We can take a better look at the different apps and how they behave. Enjoy the rooted Duo!
References:
https://forum.xda-developers.com/t/unlocking-bootloader-magisk-attempt.4162051/
https://forum.xda-developers.com/t/root-guide-updated.4266095/
https://drive.google.com/file/d/1rh_m3leEW3NAFhf-d6aIVi1rmofuWUZf/view
https://drive.google.com/file/d/1QpsywAbNroDKEDz4TytQl8UlK6v2gJSi/view