Unlocking the Power of Volatile Memory
ATRIO MK II's New 1.2.5 Update Enhances Your DFIR Framework with RAM Analysis Across Windows, MAC, and Linux.
We are excited to announce that our upcoming software release 1.2.5 for ATRIO MK II will have built-in functionality for volatile memory analysis. This will allow ATRIO to analyze RAM captures from Windows, MAC, and Linux machines. So what is memory analysis and how can you incorporate it into your incident DFIR framework?
Memory analysis is the process of examining a snapshot of the workstation's RAM to extract and analyze information about system activity. The type of data that resides in volatile memory include running processes, network connections, user activities, and potential malware artifacts. The easiest way to start analyzing a RAM capture is to use Volatlity3.
Volatility3 is the latest edition of Volatily’s memory forensic framework, which is designed to analyze volatile memory dumps from various operating systems. One of the biggest updates with this version is not having to specify the OS profile. Now Volatility uses an extensive library of symbol tables that keep track of specific location offsets for different OS types. So all you have to do is tell it the location of the memory image and which plugin you wish to run. Let’s take a look.
Install
Downloading and installing Volatility is a quick and simple process. Simply download the latest version via the Git command below:
└─# git clone https://github.com/volatilityfoundation/volatility3.git
After the download is complete, navigate to the newly created folder and install the required dependencies with the pip3 command:
└─# pip3 install -r requirements.txt
Now that it is installed, we can start to analyze our memory dump. There are dozens of different plugins for Windows RAM, but we always like to start with the same two because we feel they give us the best initial insight into what is happening on the target machine.
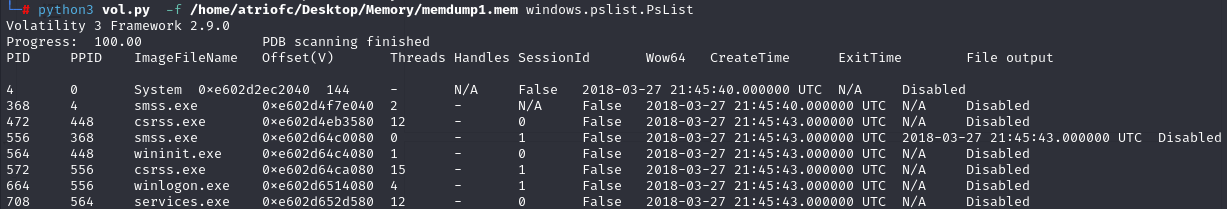
PSLIST
The pslist plugin provides a snapshot of the processes that were running while the memory dump was acquired. The plugin will provide information like process name, process IDs, and parent process IDs.
└─# python3 vol.py -f /home/atriofc/Desktop/Memory/memdump1.mem windows.pslist.PsList
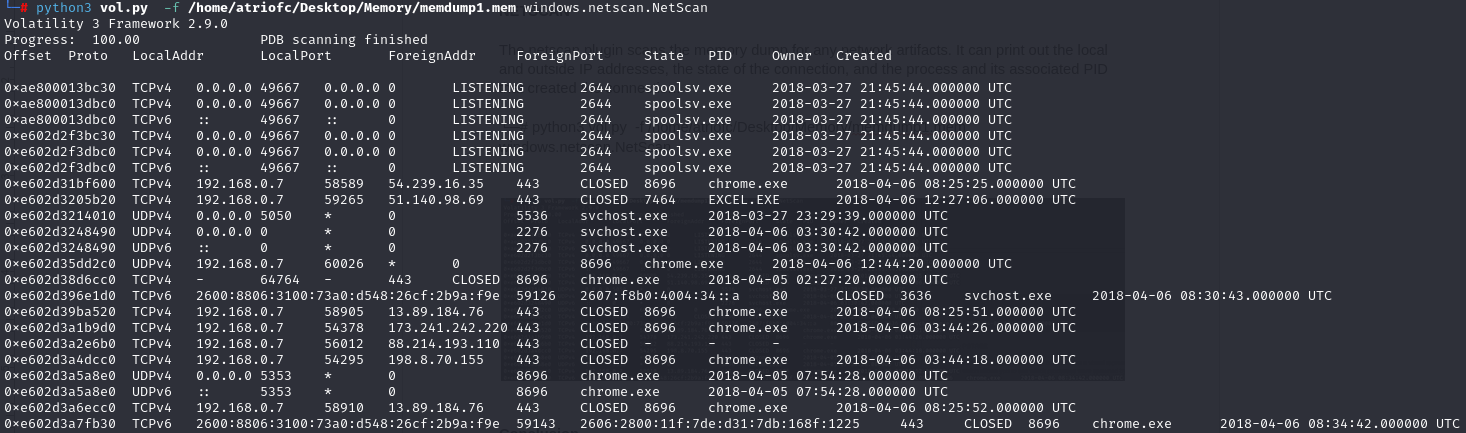
NETSCAN
The netscan plugin scans the memory dump for any network artifacts. It can print out the local and outside IP addresses, the state of the connection, and the process and its associated PID that created the connection.
└─# python3 vol.py -f /home/atriofc/Desktop/Memory/memdump1.mem windows.netscan.NetScan
Conclusion
Volatile memory analysis is crucial in today's DFIR landscape. It offers insight into the live state of the system and reveals evidence that might not be captured through traditional disk forensics. By leveraging tools such as Volatility3 for memory analysis, you can uncover hidden threats, understand system activities, and piece together the narrative of a security incident. ATRIO MK II has Volatility3 integrated into the workflow to make this process streamlined for your investigations!
Want to learn more about ATRIO’s Triage Capabilities? Request a demo!