ArcPoint Newsletter, June 2022
DF Industry Happenings
The ArcPoint Team attended the National Law Enforcement Training on Child Exploitation in Atlanta, Georgia. We met with amazing end users’ and other key partners to demonstrate how to use ATRIOTM to improve their current workflows and streamline these processes. Our CEO, Amy Moles, was able to meet all the Electronic Storage Detection K9s trained by Jordan Detection. It was tough work but someone needed to provide all the pets to these heroes!
Coming up next month, Cyber Social Hub will be hosting a live webinar on July 13, 2022, at 2:00 PM with Cesar Quezada. This is a free event and requires individuals interested to register on the website. Cesar Quezada is an experienced technical professional with over 10 years of experience in digital forensics, military intelligence, and computer systems administration. He currently supports the DoD conducting forensic examinations and is currently a Company Commander of a Cyber Security Company in the Virginia Army National Guard. He has achieved a Master's Degree in Computer Forensics and numerous forensic and technical certifications. Cesar joined the military to give back to the community and help make this country a safer place. His path to DFIR wasn't conventional and he believes that applies to a lot of practitioners. But one common trait among practitioners that he believes is we all have the desire to help make this world a safer place.
He has experienced two overseas deployments to war zones. One in uniform as a military officer and one as a DoD contractor so he knows the difficulties of getting the right people trained and equipped. He believes in empowering more people by giving them the knowledge, tools, and technology to help in that cause so working with ArcPoint absolutely fits that bill.
ArcPoint Company and Product News
The ArcPoint team has been busy adding features and testing new concepts and methods for performance enhancements. We're really excited about the performance results we're seeing and even more excited to share these with you in the future. These will be integrated into the version releases over the next few months. More on that later. In the month of May, we added some key features that we think people will find helpful.
ArcPoint added a "Not Safe For Work" AI model that will review photos for content such as nudity or that is explicit in nature. This category can be found on the AI-Object Detection reporting for photos as a new category.
ArcPoint’s R&D Engineers conducted testing on a few different data carving tools and ultimately made the switch to photorec. Testing reports concluded a 300% speed improvement in photorec over other tools we've tested and have seen consistency in the quality of the results as well.
DD images can now be processed similarly to an E01 image. If you have a .dd that was previously collected the E01 AS SOURCE feature is now E01/DD AS SOURCE. You can have multiple E01 or .dd images on a drive and ATRIO will triage all of them consecutively.
ArcPoint has set the line limit for document translation to 50 lines. This change will ensure that the user can get a snapshot of what's in a file while avoiding an unreasonable amount of time for processing hundreds or thousands of documents that need to be translated. However, upcoming products will have an expanded capability with GPU support and even desktop CPU processing power to extend past the line limit for translation of documents.
ArcPoint Presents: Unallocated Space
This month we hosted Jamie Levy. Jamie Levy is a senior researcher and developer of the Volatility Framework. She is also the Director of R&D at Huntress. Prior to this, Jamie was Director of EDR Content at Tanium, where she helped build out DFIR content for the Threat Response module, as well as various other security and DFIR-related R&D efforts. She has worked on various R&D projects and forensic cases while previously working at Guidance Software, Inc, Verizon Terremark, and SecureWorks. Check out the latest episode here!
Jamie has taught classes in Computer Forensics and Computer Science at Queens College (CUNY) and John Jay College (CUNY). She has a Masters in Forensic Computing from John Jay College and is an avid contributor to the open source Computer Forensics community.
Jamie has authored peer-reviewed conference publications and presented at conferences (OMFW, CEIC, IEEE ICC, EnFuse, ACSAC, NYBA, OSDFCon) on the topics of memory, network, and malware analysis. Jamie is a well-respected member of the DFIR community, sits on the board of directors for the Volatility Foundation, and has served on the program committee for such conferences as DFRWS, BSidesNYC, and IWCMC Security Conference (among others). Jamie is also a trainer on the topics of Digital Forensics and Incident Response, as well as Memory Forensics.
Jamie shares her story about the DFIR community and how her interest in Memory Forensics has provided her fulfillment through giving back to individuals just starting out or looking to take a deeper look into memory forensics. As an expert in the community with a working from home position, Jamie offers up great tips for balance! She shares with us how she schedules breaks throughout the day with calendar blocks, personal hobbies, and firm start-to-end cut-offs to help her unwind. This episode of Unallocated Space will be available on our YouTube Channel on June 16th. Be sure to subscribe to our channel and follow us on social media to stay up to date with the latest episodes, product developments, and company news!
Next month we are joined by Josh Brunty! During this episode, we focus on students entering the DFIR community and technical internships. The dos and don’ts of internships and how intern sponsors can make the most out of the experience for these students.
Josh Brunty is an Associate Professor of Digital Forensics in the School of Forensic & Criminal Justice Sciences at Marshall University in Huntington, WV. Prior to his appointment at Marshall University, he worked as a Digital Forensics Analyst (2005-2007), Quality Assurance Manager (2007-2008), and Technical Leader/Manager (2008-2012) for the West Virginia State Police Digital Forensics Unit at the Marshall University Forensic Science Center. He currently serves on the editorial boards of Forensic Science International: Digital Investigation, and the Journal of Forensic Sciences. He also serves as Executive Secretary and Member of the National Institute of Standards and Technology (NIST) Organization of Scientific Area Committee (OSAC) on Digital Evidence, a position he has served in since 2016. He has also served as Academician Commissioner of the Forensic Science Education Programs Accreditation Commission (FEPAC) since 2020. He is also a Fellow of the Digital and Multimedia Sciences Section of the American Academy of Forensic Sciences (AAFS).
He is currently funded by the United States Secret Service National Computer Forensics Institute (USSS-NCFI) to perform digital forensics and investigative technology research (2020-2023). He is also currently funded by the United States Department of Homeland Security Science Technology (S&T) Directorate to engage in digital forensics tools and techniques in dark web investigations (2021-2023). Additionally, he has received past funding from the National Institute of Justice (NIJ) for Technical Training, Research, and Casework Activities for state and local agencies engaged in digital forensics (2010-2015).
He has published a variety of articles and books, most notably co-authoring the Taylor & Francis textbook Social Media Investigation for Law Enforcement, which is still used in police academies and academic institutions throughout the United States. Additionally, he co-authored the Journal of Forensic Sciences article on the Forensic Inspection of Sensitive User Data and Artifacts from Smartwatch Wearable Devices, which received the 2019 American Academy of Forensic Sciences (AAFS) Digital & Multimedia Sciences Most Outstanding Research Award, in addition to being recognized by the journal as a 2019 noteworthy article.
Check out our Blog
Once a month ArcPoint releases a blog to help individuals within the community grow and expand their skillsets. Our content is intended to be used as a refresher for experienced examiners and help individuals just getting started to expand their skillsets to make investigations easier. Check out Acquire Evidence using LIBEWF on our website. Throughout this blog, we step through how to acquire evidence using the terminal on a Mac.
Want a Demo? Just Ask!
ATRIO™ is an all-in-one digital forensics hardware/software solution that performs full physical imaging and data exploitation. It is designed to be intuitive and easy to use. Output is immediately accessible in a universally-compatible, non-proprietary format and can be viewed on any computer. There are no additional software programs, dongles, or other peripherals required to operate ATRIO™. Interested in getting demo? Sign up on the ArcPoint website.
Monthly Tech Tip
Exiftool is a great open-source tool written by Phil Harvey that can extract metadata from numerous different file types. Most examiners know it can extract metadata, but not many know it can also organize files based on date.
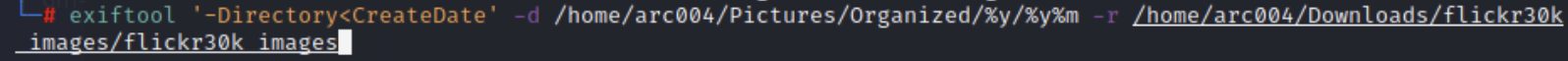
In this instance, we have a folder with a massive amount of images with random names, but we want to organize them into 2-digit Year and Month folders so that we can triage the newest images first. For that we will use this command with Exiftool:
$ exiftool '-Directory<CreateDate' -d /home/arc004/Pictures/Organized/%y/%y%m -r /home/arc004/Downloads/flickr30k_images/flickr30k_images
In this command, we are telling Exiftool to move all images from the “flicker30k_images” folder to a new folder called “Organized” and put the images in folders based on their creation date year and then year/month. This command also has the ‘-r’ to search recursively in the folder just in case there are subfolders in there.
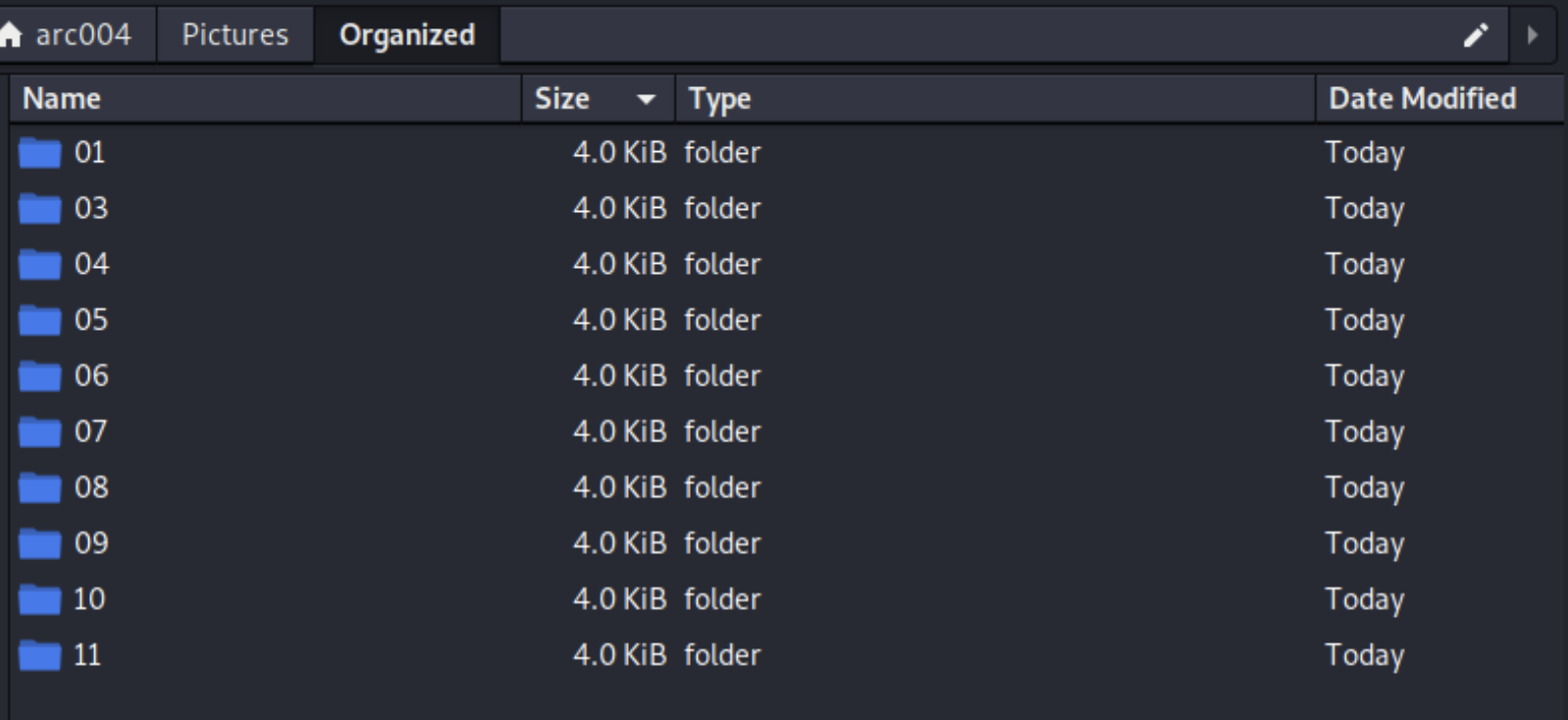
Once completed we have a folder like this:
In summary, Exiftool can be used much more than to extract metadata from files. As we can see from this example, it can be used to sort files based on dates. Admittedly it is not a perfect solution, for example, if the file has no metadata, then Exiftool will not move it to a new folder, but it is still a better solution than having a folder with thousands of random files.