Comparison of iOS backups: Encrypted vs Unencrypted
Intro
In the world of mobile device forensics, you will undoubtedly run into an iPhone. In the United States, they are everywhere and it’s common to find at least one user who has an iPhone that needs to be examined. When you come across an iPhone, you may be faced with a situation where an iTunes backup is your only alternative to get any data from the device. It may not be the best acquisition, but at least you have some data.
Why do we encrypt?
Forensic practitioners everywhere preach that you need to encrypt the iTunes backup to obtain the most data possible with an iTunes backup. But why is that? Well, it’s because Apple wants you to secure your personal information that’s contained within your backup because they know it’s easily found and easy to read. They even tell you this when you go to create a backup. It’s their attempt to get a user to essentially add a layer of security for their backup.
Setup of comparison
In this comparison, we’re going to look at an iPhone 7 running iOS 14.2. The backups were taken within minutes of each other. The images we end up with are:
iTunes backup with no password set - Unencrypted backup
iTunes backup with password set - Encrypted backup
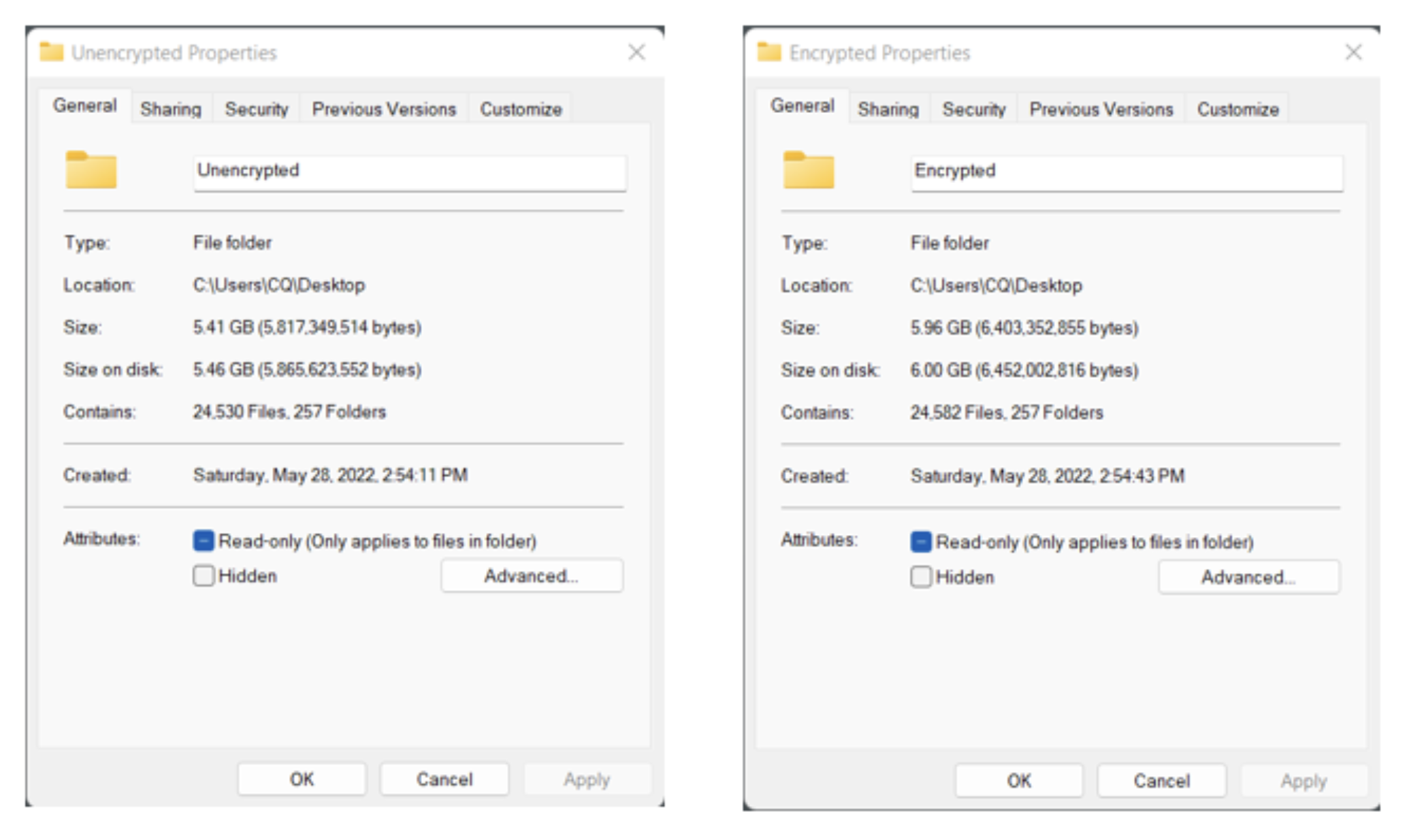
A look at the properties of each backup shows that the size difference isn’t enormous. But even though it’s not a lot, we do end up with additional data.
*Throughout this blog, the unencrypted backup will be on the left and the encrypted backup will be shown on the right.
Looking at the Data Parsed Out
Data
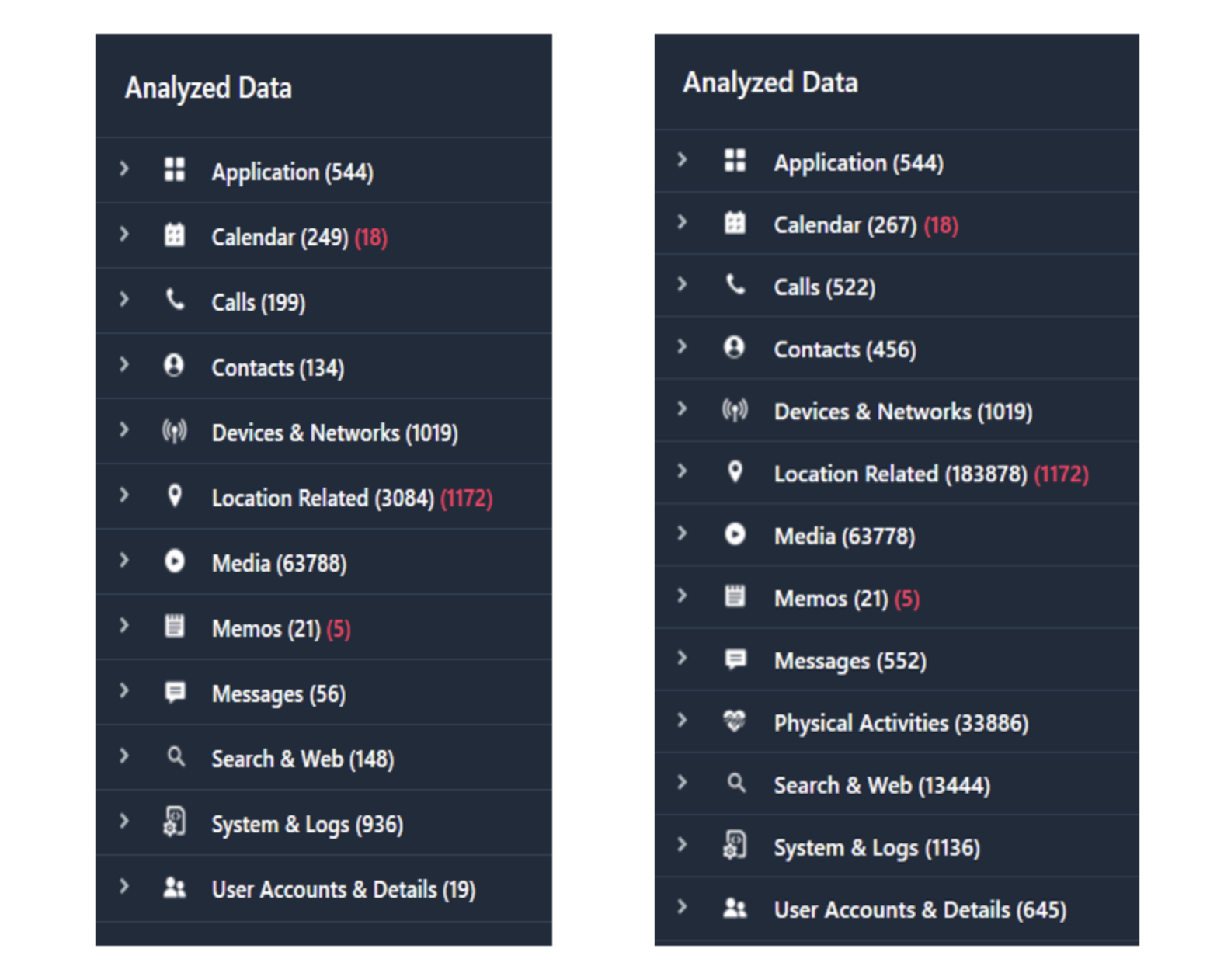
A look at the data parsed out immediately shows the difference in available information. The backups went through the same tool with the same options selected. The image on the right shows the parsed-out encrypted data with a lot more information ready to be reviewed.
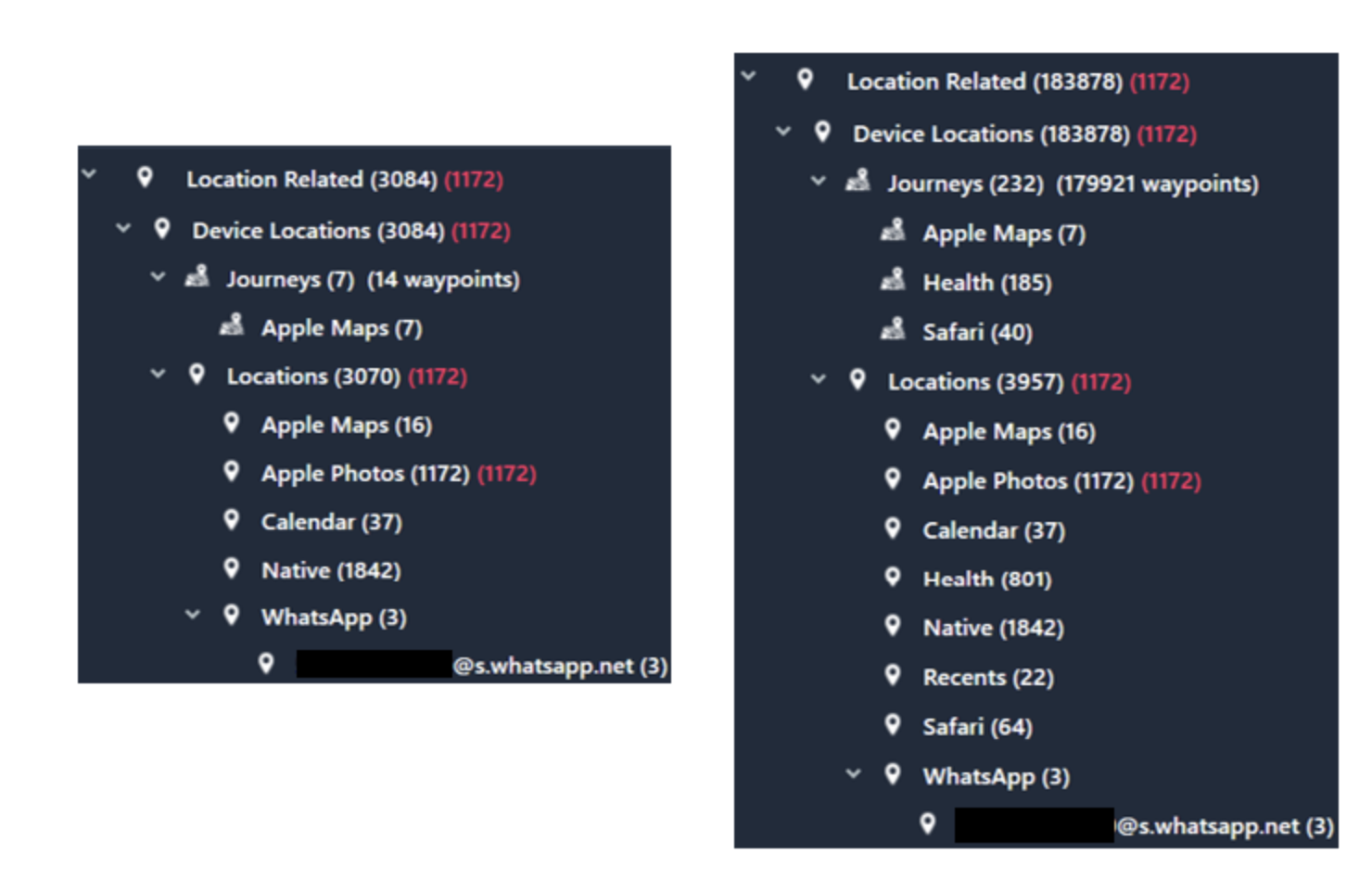
Location Data
Location data is another area where you can see the encrypted backup has more data. As noted above, if you want to back up your health data, you’ll need to encrypt it. Here we can see that indeed there is Health location data in the encrypted backup where there is none for the unencrypted backup.
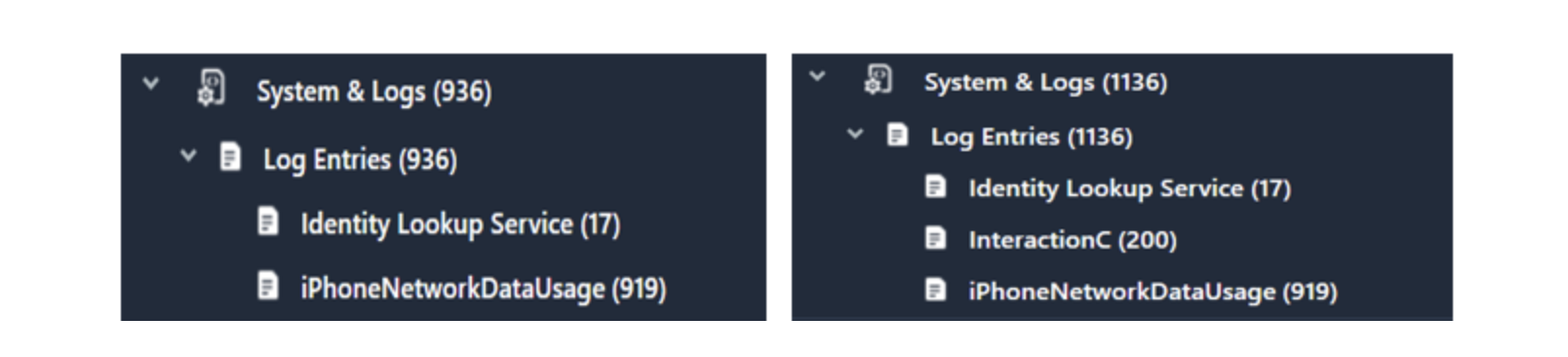
System Logs
The logs of any system are an important piece of information. In this piece of the backup, you see that you’ll get InteractionC.db data from the encrypted backup. In our instance, it was related to phone logs for this device. This can be used to show possible entries that aren’t in the normal call logs or to verify the call log entries that are parsed out.
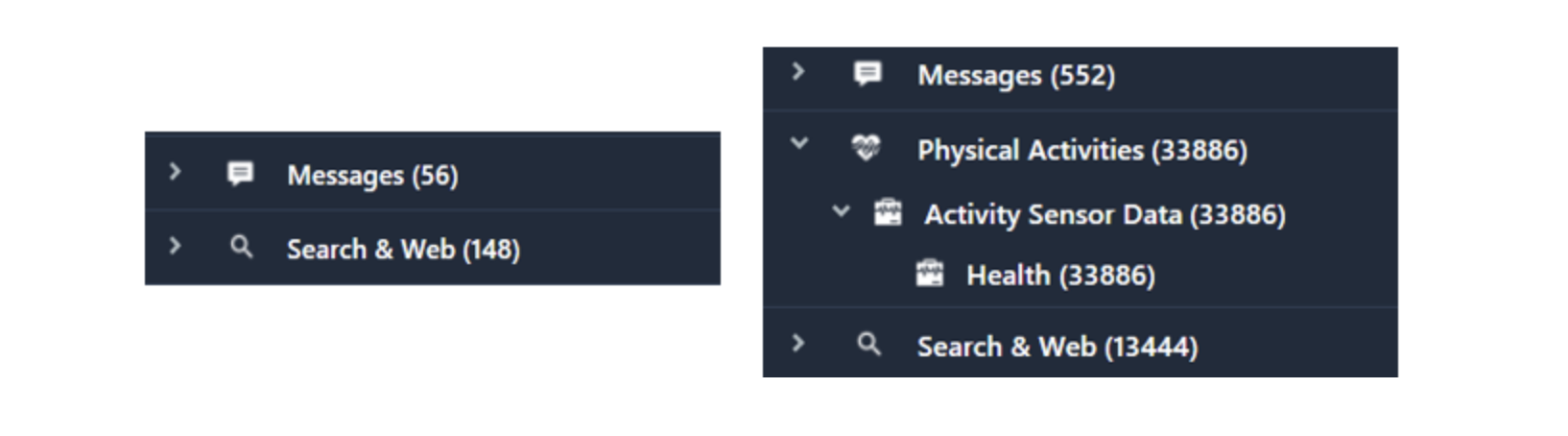
Health Comparison
And finally, the Health piece of the backup. In the unencrypted backup, there is no section at all for parsed-out data. In the encrypted backup, you see tons of data related to Physical Activity to include a user's steps, heart rate, distance traveled, energy burned, flight climbed, etc. This is one of the major selling points when telling examiners to always get the encrypted backup.
Encrypt that backup
As you can see, backups aren't one size fits all. Yes, different tools will parse out different pieces of data and different apps; but the best course of action to get the most data possible is to ensure you get as much of the data as possible. In the instance of an iPhone, that means selecting to encrypt your backup if given the option. And if you do set the backup password, don’t forget it! There have been too many instances where the person on-scene set a password to get that additional data in the backup, but the password never made it back to the forensic examiner in the lab conducting the examination. But that’s a topic for another day 😀.